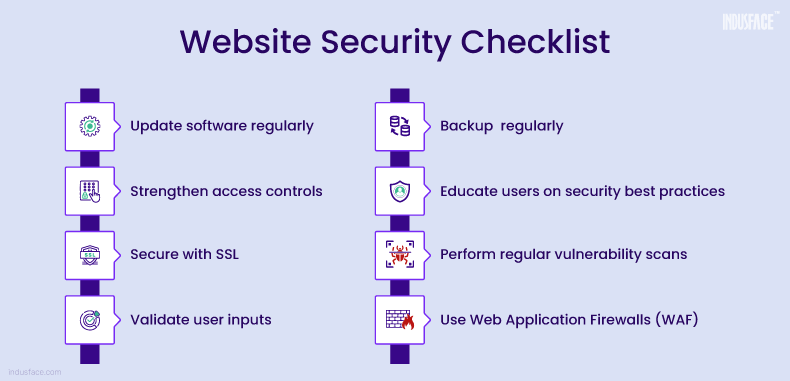
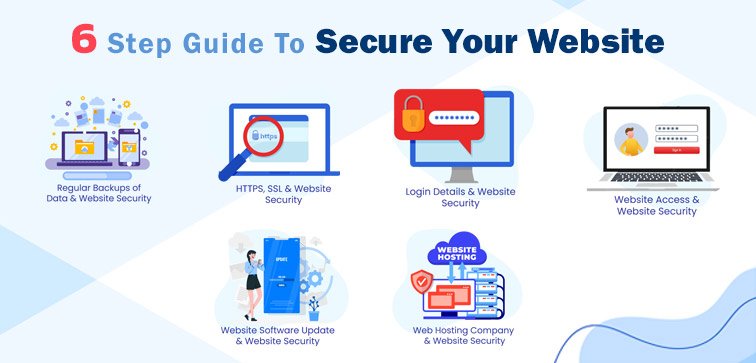
Ensuring website security is crucial for protecting sensitive data, maintaining user trust, and preventing cyber attacks. A secure website safeguards both user information and your site’s integrity. This article explores essential strategies for creating secure websites and mitigating potential vulnerabilities.
1. Use HTTPS Encryption
Encryption is a fundamental aspect of website security. HTTPS (Hypertext Transfer Protocol Secure) encrypts data transmitted between the user’s browser and the web server.
- Install SSL Certificates: Obtain and install an SSL (Secure Sockets Layer) certificate for your website. This encrypts data and enables HTTPS.
- Redirect HTTP to HTTPS: Ensure all traffic is redirected from HTTP to HTTPS. This guarantees that all data is encrypted.
- Check SSL Certificate Validity: Regularly verify the validity of your SSL certificate to avoid expiration issues.
2. Implement Strong Authentication Methods
Robust authentication helps prevent unauthorized access to your site and user accounts.
- Use Strong Passwords: Enforce strong password policies requiring a mix of letters, numbers, and special characters.
- Enable Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security beyond just passwords.
- Secure Password Storage: Use hashing algorithms like bcrypt to securely store passwords in your database.
3. Keep Software and Plugins Updated
Regular updates are crucial for fixing security vulnerabilities in your website’s software and plugins.
- Update CMS and Software: Regularly update your content management system (CMS) and other software to the latest versions.
- Patch Vulnerabilities: Apply security patches and updates promptly to address known vulnerabilities.
- Remove Unnecessary Plugins: Delete unused or outdated plugins to reduce potential security risks.
4. Implement Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) protect your website from common web-based attacks.
- Choose a Reliable WAF: Select a reputable WAF provider to monitor and filter incoming traffic for malicious activity.
- Customize WAF Rules: Configure WAF rules to address specific threats and protect against vulnerabilities unique to your site.
- Monitor WAF Logs: Regularly review WAF logs to identify and respond to potential security incidents.
5. Secure User Input and Data
Protecting user input and data is essential to prevent attacks like SQL injection and cross-site scripting (XSS).
- Sanitize and Validate Input: Always sanitize and validate user input to prevent malicious code from being executed.
- Use Prepared Statements: When interacting with a database, use prepared statements to guard against SQL injection attacks.
- Implement Content Security Policies (CSP): Use CSP to restrict the sources of executable scripts and mitigate XSS risks.
6. Regularly Backup Your Website
Regular backups ensure that you can recover your site in the event of a security breach or data loss.
- Automate Backups: Set up automated backups to create regular copies of your website’s data and files.
- Store Backups Securely: Store backups in a secure location, separate from your main server. Consider using cloud storage for redundancy.
- Test Backup Restoration: Periodically test the restoration process to ensure that backups can be successfully restored when needed.
7. Implement Secure Coding Practices
Writing secure code helps prevent vulnerabilities and protects your site from attacks.
- Follow Coding Standards: Adhere to secure coding standards and best practices for your development environment.
- Perform Code Reviews: Conduct regular code reviews to identify and address potential security issues.
- Use Security Libraries: Leverage established security libraries and frameworks to handle common security tasks.
8. Monitor and Respond to Security Threats
Active monitoring and response are essential for identifying and addressing security threats.
- Set Up Security Monitoring: Implement tools and services to monitor your site for suspicious activity and potential breaches.
- Establish an Incident Response Plan: Develop a plan for responding to security incidents, including steps for containment, eradication, and recovery.
- Regular Security Audits: Perform regular security audits to assess and improve your website’s security posture.
9. Educate and Train Your Team
Educating your team about security best practices helps prevent human errors and insider threats.
- Conduct Security Training: Provide regular training on security awareness, including recognizing phishing attempts and managing sensitive data.
- Promote a Security Culture: Foster a culture of security within your organization, encouraging best practices and vigilance.
- Update Security Policies: Regularly review and update security policies to reflect current threats and best practices.
10. Secure Your Hosting Environment
The security of your hosting environment is crucial for protecting your website and its data.
- Choose a Secure Hosting Provider: Select a hosting provider with a strong security track record and features like firewall protection and regular backups.
- Secure Server Configuration: Configure your server securely, including disabling unnecessary services and implementing proper permissions.
- Monitor Server Logs: Regularly review server logs for signs of suspicious activity or unauthorized access.
Conclusion
Creating a secure website involves implementing a range of strategies to protect against various threats and vulnerabilities. By using HTTPS encryption, strong authentication methods, regular updates, and web application firewalls, you can safeguard your site and user data. Additionally, securing user input, regularly backing up data, following secure coding practices, monitoring threats, educating your team, and securing your hosting environment are essential steps in maintaining website security. Prioritizing these practices ensures a robust defense against cyber threats and protects your online presence.